What is a phishing attack?
Cyber-attacks come in all shapes and sizes, each with their own way to breach a system.
But a phishing attack is specifically designed to trick users.
A phishing attack is like the Big Bad Wolf in Grandmas’ clothes, a malicious thing dressed up like something you trust, with dire consequences if you realise too late.
Phishing attacks usually refer to attempts made via email, but can also be conducted by a text message, social media, or by phone. The methodology is the same for all, but phishing emails are most common and most successful.
How many emails do you get in a given week?
Lots, no doubt. It’s easy to trawl through your emails, eyes glazed over, and open a phishing email, buy into its story, click the link and fill in your details. An easy mistake.
Some phishing attacks are easier to spot than others, they will feature bad grammar and spelling, as well a lack of the proper branding, of whomever the criminals are trying to impersonate.
But a well-made phishing attack will look like any other legitimate email in your inbox.
Phishing attempts utilise two things to maximise their chance of success, authority & urgency.
Authority: Well-made phishing attacks will look credible. It will be sent from a trusted brand you might expect an email from, such as Microsoft, Amazon, Apple, Google, and so on. In a targeted phishing attack criminals may even impersonate senior members of your team, and target junior employees.
Urgency: The phishing attacks compel the user to act quickly, so they are less likely to be cautious.
Safety tips for phishing:
- Be cautious of anything coming out of the blue.
- Hover your cursor over the link, does the link match what the text says?
- Bad grammar and spelling, as well as unprofessional presentation are a indication of a poor attempt at a phishing attack.
- If you are unsure about the legitimacy of a message, use another line of communication to get clarity. But do not use any communication information present in the message you are unsure of.
- Don’t follow a link, or input information until you are sure that that it is credible.
What are the damages of a phishing attack?
‘My business is small, why would criminals bother trying to trick my staff?’

Let’s say the hackers intercept a £5000 invoice for between you and your supplier. The bank details are changed, you send the payment to the hackers, not to your supplier. You’ve lost £5000, but you still owe your supplier £5000.
Guaranteed you’ve worked harder to make that money, than it is for them to steal it.
Whether you were targeted specially, or were just a random scattershot victim, hackers can make money out of you, by intercepting invoices or by holding your services or data hostage, via ransomware until you pay their ransom.
As to the extent of the damages, how long is a piece of string?
Intercepting invoices
If your system has been breached. Hackers can monitor incoming and outgoing emails for invoices and intercept them.
The criminals alter the bank account details to the fraudster’s account or an account to which they have access.
Once the changes have been made, they let the email continue to its destination. With no one the wiser, until the payee chases up inquiring after their money.
Once the money has left your account, it is gone.
There are ways to ensure you are being as safe as possible.
Always verify a change in banking information. If they are a repeated supplier, cross reference the new invoice information with that of your older invoices. If they are a new supplier get in contact with them via a second channel of communication and double check, the information is correct.
Introduced in 2020 was the Confirmation of Payee system, designed to give greater assurance that the money will reach it’s intended target.
You now need to know someone’s name if you are going to pay them, their exact name, along with all the usual payee’s details, including their bank sort code and account number.
If the name of the person you intend to send the money too, does not match the name of the account holder, you will be warned about the transaction. Do not ignore its warning casually. If you click “continue” you are taking a risk.
There are four possible outcomes that can be returned to the payer.
- Yes – the name and account type you supplied matches the details on the account.
- No – the name is a close match, but not quite. (Check your spelling to ensure an exact match.)
- No – the name doesn’t match the name held on the account.
- Unavailable – it has not been possible to check the name, because of a timeout, account does not exist, etc…
Ransomware
Ransomware gangs are still using phishing as one of the main ways to attack an organization. Once the criminals have gained the relevant login information they can install the ransomware required to hold your business hostage.
Ransomware prevents you from accessing your systems or the data held on them. Typically, the data is encrypted, but it may also be deleted or stolen, or the computer itself may be made inaccessible to you.
Simply put, you may loose computer access to your business and its data.
Following the initial attack, those responsible will usually send a ransom note demanding payment to recover access and the data. There is absolutely no guarantee that if you pay the ransom, you will regain your data, or control.
“fewer companies are giving in to cyber extortion when they are able to recover from back ups. This inflection led to a large decline in average ransom amounts paid. Stemming the tide of cyber extortion will only happen if the industry is starved of its profitability. This trend was a distinct positive during Q4.”
The Coveware Quarterly Ransomware Report describes ransomware incident response trends during Q4 of 2020
Do you have backups? Check out our Security Shield package at the bottom of the blog for more information.
Why simulate a phishing attack?
How informed are your staff about phishing attacks?
Why not find out?
By simulating a phishing attack on your staff we, and you can learn how informed they are about the dangers of phishing, without any risk attached.
“Simulating a phishing attack” may sound bothersome, but it is really simple. Your staff will be sent an email, which will contain a link, once followed it ask them for their details.
We can craft an attack. What is says, what is looks like. Our attempts will look convincing.
We can decide who it is sent to, and when.
We can see the results.
- Did they open the email?
- Did they click on the link?
- Did they fill out their details?
Crucially, if they fail our simulated attack, we can set them some User Training on phishing attacks so that they are more informed in the future.
We other a wide range of courses, from cyber security to managing to GDPR, to dozens more.
Security Shield package
Our simulated phishing attacks reveals potential weaknesses, and user training helps staff become more aware cyber security threats, removing those weaknesses, which is excellent. But more can and should be done, to make sure you are not relying solely on your staff to protect your business.
If a mistake is made, and a phishing attack succeeds, what happens your systems are breached?
That’s where the next layers of cyber security come in.
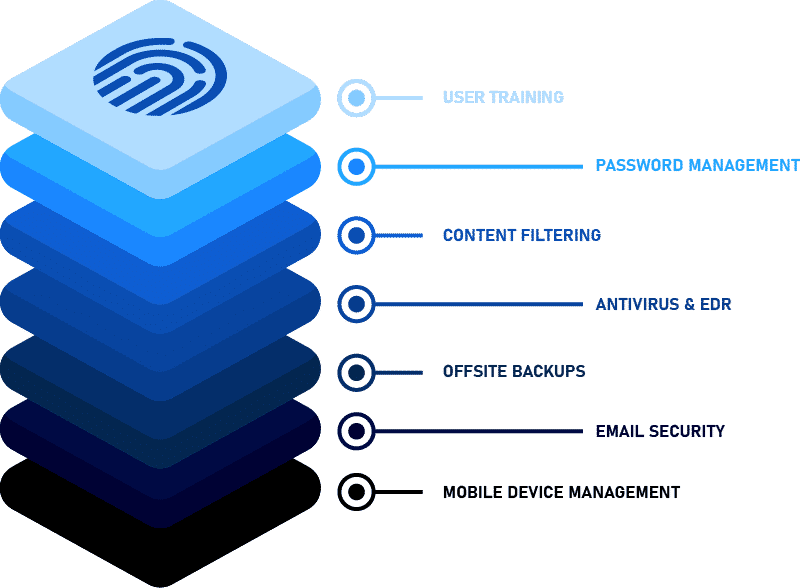
It’s our goal to put in place a multi-layered Security Shield package system to protect your businesses as much as possible with an economical solution.
User training, password management, content filtering, antivirus & EDR, offsite backups, email security and mobile device management, all these as a package for just £30 per user, per month.
With this comprehensive security package only the most determined of attacks have a chance of getting through. If your business is compromised, our package also ensures that you have the backups required to get you back up and running; and on your way to make your business better than ever
Keep your eyes open for a subsequent blogs which will explore and explain other features of our Security Shield package.




