What is content filtering?
You’ve set up your network, bought your work devices and given them to employees, all for a reason, to get the job done, whatever job that might be.
But the internet is a bit of a Wild West, one we connect to through our devices, accidently or not we can be exposed to some pretty wild things. If you do not set any protections in place.

It doesn’t have to be such a gamble on your part, content filtering sets the framework of what is secure, and acceptable on your businesses network, or on company devices.
You can establish the professional standard you want, with the security you need.
Whether it is pornography, or malware, the issue really is that these things were accessible in the first place. Our system can stop that.
Whenever a link is clicked, a URL typed, and file downloaded, it will be screened first. To see if its destination or contents, are safe, risky or malicious.
If it’s safe your page will load, your file will be downloaded without you even noticing a thing. If it is risky it will be thoroughly examined using third party data to make the assessment. Of course, if it is malicious, or doesn’t comply with your filters, it will be blocked.
Security first
In order for you to run your business smoothly, your IT infrastructure has to be equipped to handle a variety of threats. As standard practice your content filter should be configured to block access anything harmful, such as:

- Malware: Websites and other servers that host malicious software, drive-by downloads/exploits, mobile threats and more.
- Newly seen domains: Domains that have become active very recently. These are often used new attacks.
- Command and control callback attacks: Prevents compromised devices from communicating with attackers’ infrastructure.
- Phishing attacks: Fraudulent websites that aim to trick users into handing over personal or financial information.
- Potentially harmful domains: Domains that exhibit suspicious behaviour and may be part of an attack.
All these measures will create a layer of security that is preventative and automated for customers.
If you’re feeling technical here is a deeper explanation as to how our content filtering system, Cisco Umbrella operates.
Acceptable Usage
How you want your network and devices to be used, should be outlined in your Acceptable Use policy.
What is outlined in your policies, should be emplaced with your systems, in the form of content filtering. Which you can use to block all the usual suspects you’d imagine:
- Pornography
- Nudity
- Violence

Depending on what you want, or don’t want from your employees you can adjust your filters, to cover more or less.
Social media for example, is a great tool for some, or something that leads to procrastination for others. With content filtering you can finely adjust these potential issues of professionalism.
Speaking of social media, it can have security implications as well as professional ones. Careless, or malicious posting can contribute to data loss. Depending on the sensitivity of the data involved, those office selfies might not be as harmless as you might think.
Filtering access to such social media sites on your network and or devices can help with data loss prevention. But that is up to you, and what you need from your employees.
Content filters that reflect policies
Polices aren’t just there to state the niceties, they clearly express what is acceptable and safe in your business.
If you don’t have any written policies at your business, we’d recommend correcting that. It’s difficult to work to a high and safe standard if it isn’t clear what is expected of you. Read our post on creating policies here.

Remote working
With the influx of remote working it is important to set up content filters not just on your network, but on your devices as well.
Especially as those working offsite are using their own networks. Which will have no content filter, and be less secure.
Security Shield package
Our content filtering helps foster the kind of work environment you want, while giving you an extra piece of security that all businesses need. We give you the power to decide what is Secure and Acceptable
It’s our goal to put in place a multi-layered Security Shield package system to protect businesses as much as possible with an economical solution.
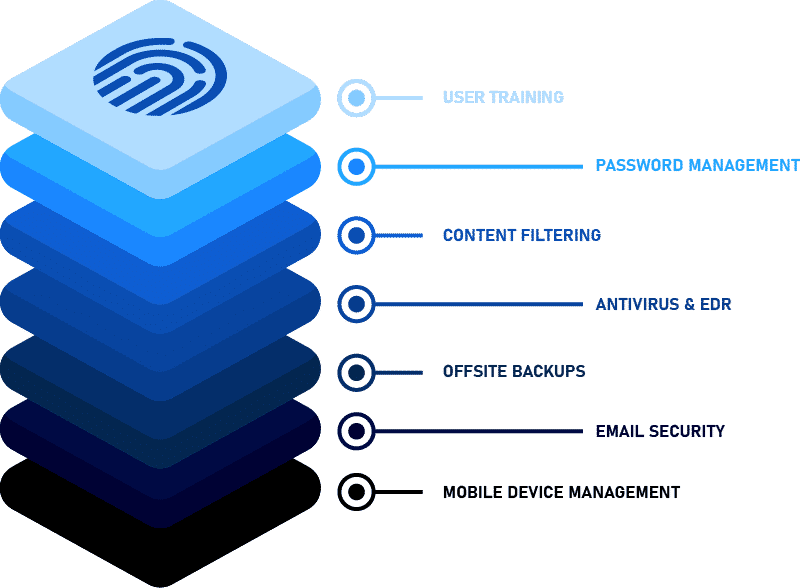
User training, simulated phishing attacks, cyber security policies, password management, content filtering, antivirus & EDR, offsite backups, email security and mobile device management, all these as a package for just £30 per user, per month.
With this comprehensive security package only the most determined of attacks have a chance of getting through. If your business is compromised, our package also ensures that you have the backups required to get you back up and running; and on your way to make your business better than ever
Keep your eyes open for a subsequent blogs which will explore and explain other features of our Security Shield package.